
HOWTO- Design and Configure a DMZ Network
By Erik Rodriguez
Tags: DMZ switch, Configure DMZ, DMZ network design, Juniper DMZ, firewall DMZ zones, multiple DMZs, Cisco DMZ switch
The following article illustrates how to design and configure the DMZ portion of a network.
Introduction
Designing a DMZ is an important part of network security. The DMZ model of choice will be different depending on the type of network. Corporate networks are usually different than data center networks, but both types require some type of DMZ. A DMZ (Demilitarized Zone) can be used for several of the below:
- Enhanced Security
- Testing/Lab Environments
- Guest Networks
Security is the main reason why a DMZ exists. However, there are two common ways to design a DMZ. The sections below will explain in detail, the pros and cons of each and what is needed to achieve each design.
Using a DMZ switch
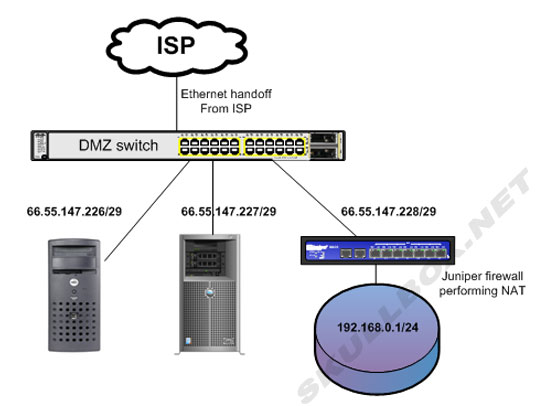
Typically a "DMZ switch" is used immediately following your Internet handoff. Devices such as firewalls, servers, and load balancers, will plug directly into a DMZ switch. This setup traditionally only provides layer 2 transport and does not perform any type of NAT, routing, or security. The idea here is that each device plugged into the DMZ switch receives a public IP address. Anything behind a DMZ switch must perform routing, security, or NAT independently. See the diagram below:
| Pros: |
Cons: |
| Easily deploy new devices using public IP addresses |
Switch is a single point of failure |
Some devices or software WILL NOT work using a NAT. If that is the case, you will need to use this type of DMZ design. A good example is a server running cPanel. The software is not supported and WILL NOT work using NAT addresses. Seriously, it won't, I have tried.
Using a DMZ switch does provide a single point of failure. If the switch fails, all the devices attached to it will lose Internet connectivity and appear down to the outside world. Careful consideration should be used when choosing a device for a DMZ switch. Enterprise switches such as Cisco, Juniper, HP Procurve, and other devices work well. Speed and duplex should also be considered depending on the type of Internet connection and the devices using it. If you have a 200 Mbps connection, do not use a switch with only 100 Mbit ports. Doing so will create a bottleneck and effective cut the usable WAN bandwidth in half. Remember by using a DMZ switch there is NO security available except the possible use of ACLs or other native port security.
Using a firewall DMZ
Most enterprise firewalls are equipped with a standard DMZ zone. This type of design is different than the previous because it generally does not use a public IP address. It is typically setup using a different private address scheme which then performs NAT on its interface. This type of design will isolate devices in the DMZ from other ports or zones on the firewall and provide the same type of protection as a DMZ switch. Generally the DMZ zones on firewalls are restricted by default so they cannot reach other zones on the same device and vice versa. See the diagram below:
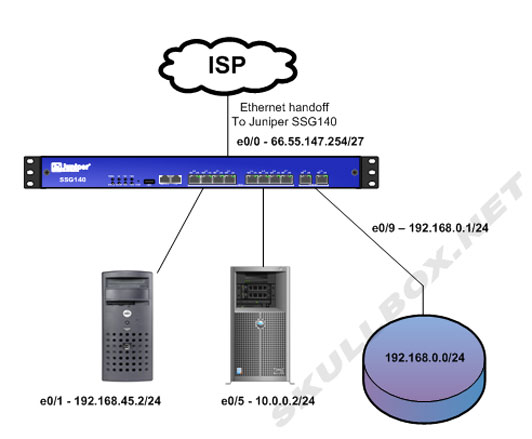
Pay special attention to what operations the firewall is performing above. First, there is no DMZ switch. The firewall is connected directly to the ethernet handoff from the ISP in port e0/0. It has a public IP address of 66.55.147.254/27. That leaves 66.55.147.227-66.55.147.253 left as usable IP addresses. As you can see, there is also a server which is plugged into port e0/1 with an IP address of 192.168.45.2/24. This server reside in an independent zone (VLAN) which isolates its traffic from the rest of the zones. The firewall is using a MIP (mapped IP) of 66.55.147.253 --> 192.168.45.2. This effectively NATs all traffic destined to the public IP address and then to the internal address on port e0/1. The same configuration applies to port e0/5 only using a different public IP address, 66.55.147.252. The firewall rules control which protocols and source networks are allowed to pass through the firewall. The last interface e0/9 is also in a different zone just like the other 2 devices. However, this zone is used for a corporate LAN. Unlike the MIP addresses used by the servers, all machines in the e0/9 zone will appear to come from 66.55.147.254, the main IP of the firewall. The SSG140 is performing NAT for the entire 192.168.0.0/24 network. If devices from that network need to communicate with port e0/1 or e0/5 a firewall policy will need to be created. Juniper firewalls are covered extensively in another section of this site.
| Pros: |
Cons: |
Internet traffic travels through single device
Granular ability to control traffic
|
Switch is a single point of failure
Cannot use public IP addresses directly on other devices*
|
For troubleshooting purposes, it is better to have all Internet traffic flowing through one device. Things like broadcast storms, network loops, and large amounts of bandwidth usage are easier to troubleshoot trough a single device. Using the DMZ switch as mentioned above could take more time as you may need to troubleshoot each device attached to it individually. By using a firewall you also have a granular ability to control what networks/protocols can communicate between your DMZ(s) and other zones. This may be difficult or impossible using a DMZ switch.
On the negative side, a firewall is also a single point of failure. A firewall device failure would result in all zones being unreachable to the outside Internet just like the failure of a DMZ switch. However, most enterprise firewalls can be configured as clusters and will resume all the sessions and traffic flows if the primary device goes offline. Network administrators should pay careful attention to overall throughput of their firewall. Most firewalls will not do true 1Gbps. If different zones need to communicate at a specific speed, spec the firewall accordingly. Last, unless you have more than 1 allocation of public IP space, you cannot use public IP addresses within your firewall DMZ(s). See the following for more details on using Public IP addresses behind firewalls.
Contact Us
NOTE: this form DOES NOT e-mail this article, it sends feedback to the author.
|
|
