
|

|

|

|

|

|

|

|

|

|

|

|

|

|

|

|

|
|
|
|
|
|
|

|

|

|

|
|
|

|
 |
|
|
|
|
Mailing List
|
|
By Joining the mailing list you will be notified of site updates.
|
|
Show Your Support For
This Site By Donating:
|
|
|
|
|

|
|
|
|
|
|

Using public IP addresses behind a firewall
By Erik Rodriguez
Tags: firewall with public IP addresses, Juniper firewall setup, IP addresses behind firewall, slash notation
The following article illustrates how to configure the use of public IP space on the trust side of a firewall. This is common in data center networks and other networks that require the use of public IP space with the protection of a firewall. There is also information on the combination of public IPs and NAT on the same device.
Introduction
Traditionally, IP space is allocated and all devices behind the firewall are configured with NAT addresses. This works well most the time, but there are cases where public IP addresses need to be assigned to servers or devices directly. In order to accomplish this, you will need at least (2) different allocations from your ISP or network administrator. One will be used as your connection to the public Internet. The 2nd or rest of the allocations will be for devices "behind" or protected by your firewall. This is commonly referred to as the trust side or trusted zone of your firewall. If you are not familiar with "slash notation" see the subnet cheat sheet.
Device and provider configuration:
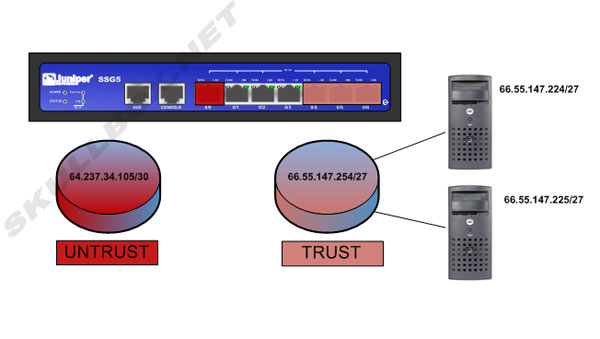
For this example, let us say an ISP has provided two IP space allocations for our firewall. They provide an allocation of /30 for the Internet facing side and an allocation of /27 for the trust side.
The /30 will provide (2) usable IP addresses*:
64.237.34.104
64.237.34.105
The /27 will provide (29) usable IP addresses*:
66.55.147.227 - 66.55.147.254
*Remember that with IP address allocation, you lose 3 IP addresses for the network, broadcast and gateway to your provider. With a /24 allocation (say 66.55.147.0/24) you will be unable to use 66.55.147.0, 66.55.147.255, and whatever the provider uses as a gateway. This is usually 66.55.147.1.
The 2 IP addresses from the /30 will need to be used on the provider side and the Internet facing side of the firewall. In this case, 64.237.34.104 will be the gateway (provider side). The other IP (64.237.34.105) will be assigned to the Internet facing side (also called the untrust side) of the firewall. An IP address from the /27 will also need to be assigned to the trust side of the firewall. In this case, we will use 66.55.147.254. Here is where the tricky part comes in. The provider MUST statically route 66.55.147.254/27 to 66.237.34.105. This will tell the rest of the Internet that it must go through 64.237.34.105 to communicate with any address with 66.55.147.254/27. Last, a default route must be added in the firewall for 64.237.34.104. This will allow traffic to leave the firewall, travel through the providers network, and out to the internet. See the diagram below:
Public IP addresses can also be used in conjunction with NAT on the same device. For information see Public IPs and NAT on the same firewall.
Contact Us
NOTE: this form DOES NOT e-mail this article, it sends feedback to the author.
|
|
|
|
|
|
