
IDS - Intrusion Detection System
By Erik Rodriguez
This article provides some information about intrusion detection systems. IDSs should be used in all networks small to large. It is a critical second stage of security after your firewall.
What is an IDS?
A system that tries to identify attempts to hack or break into a computer system or to misuse it. IDSs may monitor packets passing over the network, monitor system files, monitor log files, or set up deception systems that attempt to trap hackers.¹ With that being said you get the basic idea. While a firewall should always be your first line of defense, an IDS should be next. I use a simple analogy. Think of your network as a prison. The outside is protected by a large wall (firewall), while the inside is protected by cameras and corrections officers (an IDS).
How does an IDS work?
While there are several types of IDSs, the most common types work the same. They analyze network traffic and log files for certain patterns. What kind of patterns you may ask? While a firewall will continually block a hacker from connecting to a network, most firewalls never alert an administrator. The administrator may notice if he/she checks the access log of the firewall, but that could be weeks or even months after the attack. This is where an IDS comes into play. The attempts to pass through the firewall are logged, and IDS will analyze its log. At some point in the log there will be a large number of request-reject entries. An IDS will flag the events and alert an administrator. The administrator can then see what is happening right after or even while the attacks are still taking place. This gives an administrator the advantage of being able to analyze the techniques being used, source of attacks, and methods used by the hacker.
Specifications for IDS
IDSs are defined by what is called the Common Intrusion Detection Framework (CIDF). It is composed of 4 components:
- A boxes - Network activity analysis devices that can be specific hardware, software or both.
- C boxes - Countermeasure mechanisms or response procedure equipment.
- D boxes - Storage mechanisms (hard Disks), which are essentially the logging equipment.
- E boxes - These are considered event generators, commonly known as sensors.
|
²
|
A boxes
A boxes work like the situation mentioned above. They gather information and look for defined patterns. These patterns can include the consistent stream of packets by Trojans or viruses. An A box is great for detecting DDoS attacks and router attacks. Think of an A box as an "alarm."
C boxes
C boxes work a little differently than A boxes. After an attack has been detected, C boxes have the ability to provide countermeasures. This could include locking a user account or modifying the ACL (Access Control List). Think of a C box as a "counterattack." These work better because they save the administrator from dealing with every little flag. These are valuable in large or enterprise networks.
D boxes
D boxes are rather simple. They provide a means of logging data. One of the best practices for protecting a Linux/UNIX server is to record the logs to a different machine. This works the same way. Servers and IDSs may send their logs to a D box that serves only as a repository. D boxes are important because you may need to analyze data at anytime, even after a C box has taken action. Think of a D box as a "dump server."
E boxes
E boxes are a very important part of an IDS. While an E box cannot be an IDS on its own, without an E box, an IDS cannot function. The function of the E box is simple, it produces "events." Events are not always suspicious. An event can be as simple as recording a user logging on to a server. Think of an a E box as an "event creator."
It is important to know how the term "boxes" is used. While the term "boxes" does not actually refer to physical machines, these "boxes" can and often are used in combination. For example, IDS software can utilize a combination or all of the above framework.
Types of IDS
Generally speaking, there are 3 main types of IDSs:
- Suspicious Detection
- Abnormal Detection
- Signature/Pattern Detection
The suspicious detection is used to flag a defined activity. For example, a firewall may or may not block a port scan. Suspicious detection will automatically flag this event, record the source IP, and the ports scanned. This type of detection is usually customized. System administrators will need to specify what activity qualifies as "suspicious."
The abnormal detection is usually customized as well. It does what its name describes. It looks for abnormal behavior. How is this different from suspicious detection? Here is an example; Most corporate LANs are only active during business hours. From 9 AM - 6 PM, the servers are active, users are logged on, and the routers are busy. However, during non-business hours, the network should be rather stagnant. This is where the abnormal IDS comes into play. In the event that a workstation on your network is infected with a Trojan, the hacker could use that machine to gain access to the rest of your network including the file servers. Usually, this is late at night when the administrator and users won't notice. An abnormal IDS would record network activity and file requests during non-business hours. So, if a users was all of the sudden requesting files from server at 2 AM, the abnormal detection IDS would send a red flag. This allows network administrators to know exactly what is going on when they are not there.
The signature/pattern detection relies heavily on a database of, you guessed it, signatures and patterns! This means the known probing tools, like the ones used by "script kiddies." The common Trojans that are all over Mirc, and various worms have a consistent pattern of how they send and receive data. A database will include the signatures or patterns used by these programs. It constantly monitors the network and when there is activity that matches something from the database, the red flag goes up. This is helpful for large networks. Especially if the users are ignorant and download things they shouldn't...
The best IDSs use a hybrid approach by including 2 more of these detection methods. System administrators should be careful not specify rules that are too harsh. Going over-board can lead to false positives and unwanted chaos. However, it is important to specify rules that will catch intrusions.
Putting it all together...
IDSs can come in the form of hardware, software, or both. One example is the hardware based Enterasys Dragon IDS. This device employs a "network sensor" and "active response" technique to protect a network. The image below shows a Cisco WS-X6381-IDS. This device uses both hardware and software. Physically, this device is attached to an intermediate or core switch. The presence of a hard drive entails its use of software to analyze results.

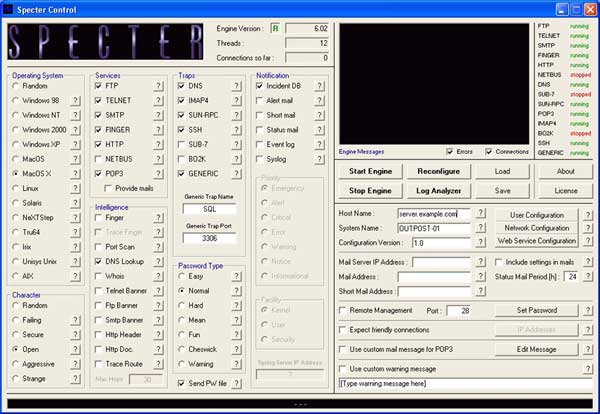
On the software-based side, a program called Specter, looks like a great program. A rather steep price (retails for $899) makes this software un-attractive to small networks or organziations with a low budget. Although, it runs on any version of Windows and can emulate practically any system. I have not used it, but here is a screen shot of the interface.
Deploying an IDS
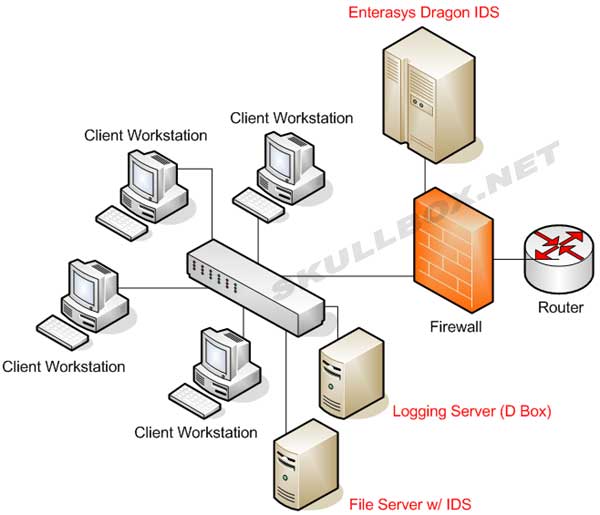
An IDS can play pretty much any role you need it to play. For instance, software can be installed on a workstation (like specter) to monitor requests from other parts of the network or outside traffic. An IDS can also be used in conjunction with other network devices. The diagram below shows an example of setting up a dedicated machines with IDS software. Notice the Enterasys Dragon is located in the DMZ. Placing a decoy in the DMZ will deter hackers from the rest of the network. Taking the time to trip the IDS gives system administrators time and data to analyze. This in-turn helps them protect the network.
The most efficient technique to deploying IDSs on your network is proper analysis. Don't go overboard right away. Analyze the way your network is setup. Every system administrator knows the potential weak points of their network. Setting up an IDS may take some time to get everything working right. Trial and error will always be an important tool for tuning up everything and getting it just the way you want.
¹ http://myphliputil.pearsoncmg.com/student/bp_hoffer_moderndbmgmt_6/glossary.html
² Mairs, John. VPNs: A Beginners Guide, Berkeley, CA: McGraw-Hill, 2002
|
