
Firewalls
By Erik Rodriguez
Tags: types of firewalls, NAT firewall, Juniper Netscreen, firewall security, firewall configuration
This article contains information about different types of firewalls, their operation, and implementation.
What is a Firewall?
A firewall is a system designed to prevent unauthorized access to or from a private network. Firewalls are now widely used because of the vast amount of broadband connections present. They provide a first line of defense for your computer or network. If it succeeds in keeping the bad guys out, while still letting you happily use your network, it's a good firewall¹. Every corporate network has at least one firewall in use. Firewalls come in all shapes and sizes. Most computers are shipped from the factory with some type of firewall software or may use the default firewall built into XP.
Types of Firewalls
There are two main types of firewalls: hardware and software. High Level Hardware firewalls are very expensive and are not practical for the home user. However,
low-end routers that perform NAT act as a hardware firewall. Cheaper broadband routers such as Linksys, Belkin, D-Link, etc provide this functionality. In a corporate environment, expensive devices like the Cisco ASA and Juniper SSG are commonly used hardware solutions. Hardware firewalls allow for more complex configurations and often incorporate things like VPNs and advanced security features.
Software firewalls are practical for home users because they are nothing more than a program that runs with your operating system. These programs are usually
inexpensive, free, or come built into the operating system. They are many different types of firewalls available with many different options.
Hardware vs. Software
Generally speaking, hardware firewalls perform better than software firewalls for several reasons. First, a hardware firewall is "dedicated" to inspecting traffic.
Unlike a software firewall, it does not compete for CPU time or RAM. The main downside to a hardware solution is cost and configuration. High-end devices like Cisco's PIX firewall can be tricky to configure. Software firewalls are easy to install and generally easy to configure. If you are on a network with other clients that you do not know, such as a dorm or apartment with shared Internet access, a software firewall is a must! Remember that if your router performs NAT, it only protects you from Internet traffic. You are still vulnerable to attacks from within your LAN. Hackers often target routers to gain access to other devices or machines on a network.
Examples
Let us say Susan has a DSL connection at home. From there she does her banking, stock trading, and other private communication. A firewall is important because it would block connection attempts by a hacker. If a hacker has Susan's IP address, he can establish a remote connection. If a successful connection is made, it is possible for that hacker to intercept passwords or other data that endangers Susan's online identity. Are you wondering if a firewall is for you? I'd say "Better Safe Than Sorry." You wouldn't want to own a store in a dangerous neighborhood without a burglar alarm. Below are diagrams of how a firewalls can be deployed in a network:
Simple NAT Firewall
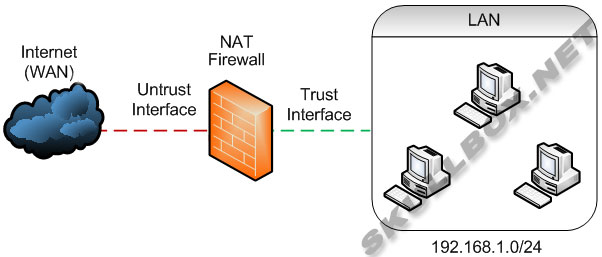
The diagram above illustrates the firewall protection provided by NAT. While 3 machines are attached to the router, the Internet/WAN link thinks only 1 device is present. This protects all 3 machines by limiting access to IP addresses and ports from the Internet/WAN connection. For more details on this see the article on NAT.
Contact Us
NOTE: this form DOES NOT e-mail this article, it sends feedback to the author.
|
¹ Zwicky, Elizabeth; Cooper, Simon; Chapman, Derek. Building Internet Firewalls. Sebastopol, CA: O' Reilly, 2000.
|
