
|

|

|

|

|

|

|

|

|

|

|

|

|

|

|

|

|
|
|
|
|
|
|

|

|

|

|
|
|

|
 |
|
|
|
|
Mailing List
|
|
By Joining the mailing list you will be notified of site updates.
|
|
Show Your Support For
This Site By Donating:
|
|
|
|
|

|
|
|
|
Audience: Newbies - Self Learners
Last Updated: 3/21/2011 6:56:12 AM
Original Creation Date: 10/16/03 5:21 PM
**All times are EST**
|
|

Hacking Linksys Routers
By Erik Rodriguez
I am not responsible for misuse of this information.
This article describes how I was able to find linksys routers open to vulnerability. If you have a Linksys router make sure you have taken the proper steps to
securing yourself. There is a follow up to this article here.
I scanned a rather large portion of IP's (2 class C IP ranges). If you don't know what port scanning is click here. There are several
important things you should know before I go further. This is a violation of most ISP's "acceptable usage policy." For that reason, I targeted the end consumers NOT corporate or commercial connections. Now, if your going to port scan a large range of IP address I suggest that you specify only the ports you need. Don't scan every port because it will take FOREVER! In my case, I scanned for the following ports:
- 21: FTP
- 22: SSH (usually a *nix system or some kind of server)
- 23: Telnet
- 80: HTTP
- 8080: Alternate HTTP (some ISP's block port 80, by default some routers will run on 8080)
- 3389: RDP (Microsoft remote desktop connections run on this port)
I used a program called Networkview. It's pretty simple looking but it gets the job done. The image
below shows a small portion of my results (I scanned over 300 IP's)
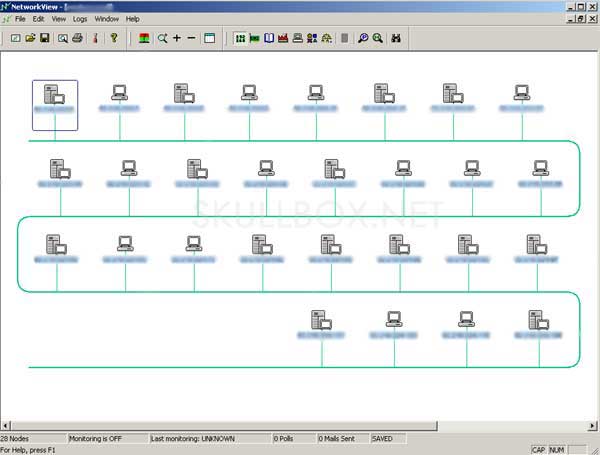
Notice the node with the red box around it. It has a different icon than most of the other nodes. This indicates that one or more of the ports I specified is open
on that node. Based on what port it was I could make a pretty darn good guess as to what was running on that machine. Here are my complete results based on 314 IP's
reported:
| Port |
# Open |
Identity |
Password |
| 21 |
26 |
FTP sites |
Some anonymous with WAREZ |
| 22 |
3 |
A few Red hat servers |
All had non-standard passwords |
| 23 |
15 |
Some Cisco devices and high end routers or modems |
All had non-standard passwords |
| 80 |
0 |
This port was blocked by the ISP |
N/A |
| 8080 |
24 |
Mostly routers or personal web servers |
Almost half Linksys routers with default login |
| 3389 |
9 |
A few Windows 2000 servers, mostly XP Pro |
1 with a guest account active over RDP |
I gained access to these routers using the standard login credentials (admin:admin). This combination is used as the router leaves the factory. It is up to the user to change the password manually. This is why so many of these routers are still using the default credentials. As the results show, nearly half of the routers running with web-management enabled were using the default login credentials. (shown below)
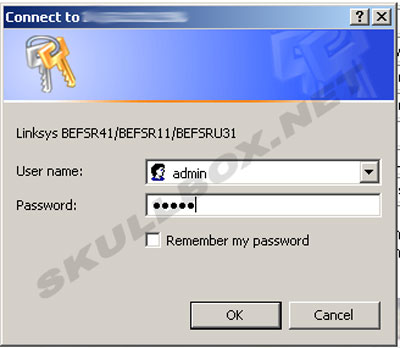
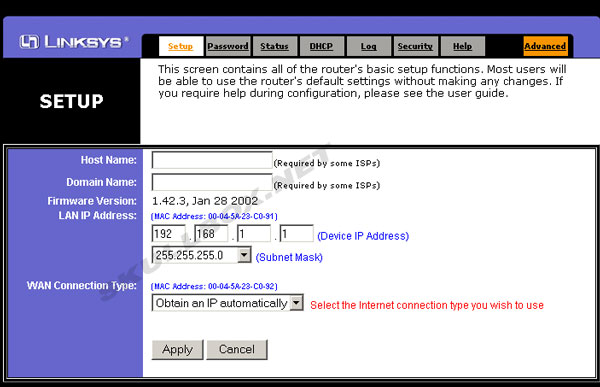
Upon Successful login, I had to option to change the password, change the client connection rules, and even re-direct traffic. A hacker could setup the router to
leave a specific machine completely open to the outside network. The web-management setup is shown below.
In conclusion, I suggest that anyone using a router to share their broadband connection change the router password, and ensure web-management is not enabled. Make sure your router has the latest firmware installed.
|
|
|
|
|
