
|

|

|

|

|

|

|

|

|

|

|

|

|

|

|

|

|
|
|
|
|
|
|

|

|

|

|
|
|

|
 |
|
|
|
|
Mailing List
|
|
By Joining the mailing list you will be notified of site updates.
|
|
Show Your Support For
This Site By Donating:
|
|
|
|
|

|
|
|
|
Audience: Newbies - Self Leaners
Last Updated: 03/21/2011 1:50 AM
Original Creation Date: 2/05/04 3:51 AM
**All times are EST**
|
|

Telnet Hacking Part 2
By Erik Rodriguez
I am not responsible for misuse of this information.
This article describes how telnet servers are used as resources for hacking.
Overview
If don't know what telnet is here. The content of this article is based on this concept. Most
telnet servers give you the ability to "telnet out." This means that you are using the telnet server as an access point to reach your destination or target.

Remember that telnet can run on all different devices. Regular Windows boxes like 2000 & XP both have telnet pre-installed as a service.
Linux boxes can run telnet or SSH. Most servers are now using SSH instead of telnet because it is more secure. In my
opinion, the best source for telnet "hopping" is a router or switch. This is because routers and switches are usually not monitored as closely as servers or
workstations. The logging system of a server can be complicated. In some cases, logging systems can span across multiple machines and backup devices on a network.
Generally, there is a much greater chance someone will notice you logged into a server than a router or switch. All high-end routers like Cisco, 3com, Nortel and
even some lower-end products run telnet. The easy way to find these devices is to port scan. If you conduct a scan of a network and find port 23 active, it's a
telnet server.
Telnet Capabile Devices
From the results of my research I found a somewhat popular modem/router combination that runs a telnet server with a huge security issue. They are produced
by a company called Netopia. I have owned a few of their products at one time or another over the years. Even worse than the
default Linksys passwords, these routers are shipped from the factory with NO PASSWORD PROTECTION AT ALL.
These models run without passwords by default:
Click For Images
Cayman DSL modem/router*
Netopia R910 modem/router
*Cayman is a product line of Netopia.
The Cayman model is slightly better than the Netopia model because it offers a full CLI (command line interface). The netopia is menu-driven but still offers most of
the features the Cayman does. If you are wondering how you would ever find one with the number of people using broadband, its basically the luck of the draw.
Randomly scanning IP's to find such devices can take a while. However, if you find one or two, you may be able to find more. These are generally 2 or 3 times the
price of the more commonly used equipment. Someone using one of these devices may have received it from their ISP as a part of a service agreement. This means there
may be more on the same IP range. Believe me when I say plenty of them are password protected because some cable/DSL companies have realized this and sent notices to
their customers. Although, with the size of the Internet there are still plenty open devices out there.
Now What?
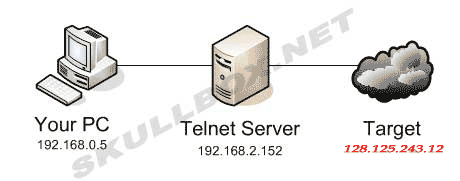
The idea behind using a telnet server to connect to other systems is to hide your real IP address. The IP addresses used in this article are not real, but still represent the concept accurately. If you connect to your target (128.125.243.12), the address logged would be the telnet server (192.168.2.152), not your real IP address (192.168.0.5). Remember, the more telnet servers you hop through, the better. Using 1 telnet server does next to nothing because your ISP most likely has a record of what telnet sessions you have connected to and could make a match from both ends. Believe me you would be surprised what your ISP can find out. Some say that they only track your bandwidth usage, but with Carnivore working at most ISP's they can dig up almost anything. The safest way to connect to devices is to establish a connection to an SSH server first. From there, any connections made from an SSH server would be undetectable by an ISP because SSH uses secure channels. Your ISP would only be able to tell that you were connected to an SSH server, and not what you were actually doing with that server. High-profile hacks are very complicated and can span across multiple devices (as many as hundreds) making it impossible to track the source IP address. Often times a hacker will use a dial-up account (that isn't theirs) or a public location, hop through telnet devices and make their attack. The image below shows a digram of the connections I discussed above.
Public Telnet Servers
There are public telnet servers available for many different reasons. Some are for chatting, news, email, etc. They are not as common now because we have better ways of doing things now (HTTP, FTP, AIM, etc). Most of the public servers will not allow you to telnet out. However, there are still some out there. I have found a few route-servers that allow you to telnet out. Although, using a route-server is a really bad idea because an ISP has the ability to log EVERYTHING! Some route-servers even advertise the fact that they log everything.
Conclusion
Remember that all these devices have logging capabilities. Logs are the easiest way to track someone. However, a good hacker will know how to manipulate or clear
the logs to "clean up." Also, using a telnet device to remotely access a target is not the same as a DoS attack. While they are both viewed as malicious activity, they are not synonymous. For information on DoS attacks click here.
|
|
|
|
|
